Emerging threats in national security: Connected at the edge
In the UK's journey in establishing connected places or “smart cities”, the focus is on harnessing technology to enhance the quality of life for UK citizens. These advancements in managing urban and rural environments provide tangible benefits; reducing pollution, optimising resources, improving public services and reducing crime. However, the concept of connected places encompasses a system of distributed edge devices; sensors, networks, applications and observational equipment, which opens up avenues for cyber attacks that could cause significant harm to our overall national security posture.
The use of connected edge devices are also critical in other arenas - in defence and within the intelligence community. The threats here are arguably more acute, but the same principles of Zero Trust, which are set out below, can be applied to drastically de-risk those systems.
National Security in the Context of Connected Places
Connected places use a combination of wired and wireless network devices that collect and process vast volumes of personal, business and government data, produced through everyday interactions. This data can provide valuable insights for threat actors, including profiles and patterns of life of the British public and the intrinsic operations of critical infrastructure. In the hands of a threat actor, this data can be exploited to enable espionage, exploitation of individuals and foreign interference with critical infrastructure. Protecting these physically distributed systems is crucial for safeguarding national security.
Parliamentary Discussions have raised concerns about the security of connected systems, highlighting the focus on stringent cybersecurity measures. Additionally, the NPSA (National Protective Security Agency) has published Connected Places related legislation, regulations & guidance that builders and maintainers of connected places need to be aware of.
Adapting to Zero Trust Security in Connected Places
To address the security challenges of connected places, every network, user device, application and transaction should be treated as hostile. No device or user, regardless of their location or network, should be automatically trusted. Instead, constant verification, dynamic access controls and mutual end-to-end encryption should be applied to secure the data being transmitted, stored and processed. Any access to a network from a threat actor would be counterproductive because everything is encrypted and the root of trust is protected by non-digital means.
Implementing Zero Trust in Edge Devices
Continuous Verification: Verifying the authenticity and integrity of edge devices with every interaction ensures that only legitimate devices have network access. Authentication is enforced with every interaction - no device is assumed to be trusted.
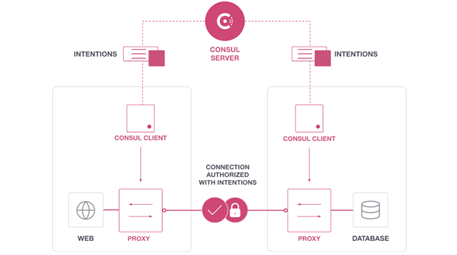
HashiCorp Consul service mesh enables automatic service-to-service encryption, and identity-based authorization. Consul uses the registered service identity, rather than IP addresses, to enforce access control with intentions. Intention enforcement is network agnostic, so Consul service mesh works with physical networks, cloud networks, software-defined networks and edge networks where there could be intermittent connectivity.
Dynamic Access Control: Implementing human authorisation based on identity, access control based on least privileged access and the instant revocation of access when nefarious behaviour is detected is crucial for securing edge devices in a connected environment. Traditional solutions for safeguarding user access creates risks around credential sprawl and users having access to entire networks and systems.
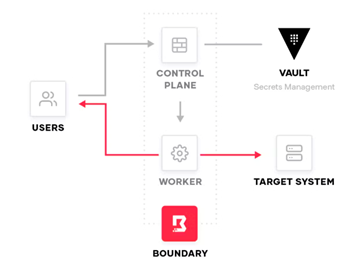
HashiCorp Boundary simplifies secure remote access to dynamic hosts, services, and edge devices without managing credentials, IPs, or exposing your network.
Data Encryption: Encrypting data at rest on edge devices, in transit from edge devices to central systems and at rest on central systems is essential for maintaining data confidentiality and integrity.
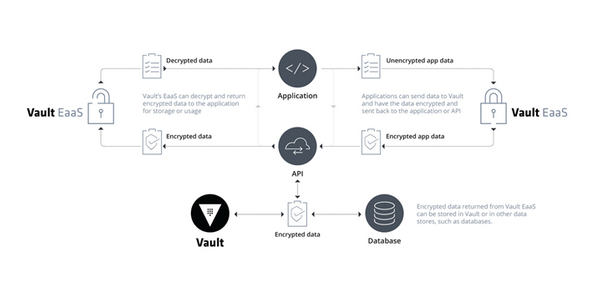
HashiCorp Vault provides Encryption as a Service (EaaS) to enable security teams to fortify data during transit and at rest. So even if an intrusion occurs the attacker would never get a hold of the raw data.
Pragmatic application of Zero Trust
Ultimately, there is always a balance between security and usability. If one was simply tasked with designing the most secure system possible, it would likely be a closed loop that was inaccessible by humans and not connected to any network. The reality in designing a system for connected places means that data needs to flow across networks that the service provider does not own, devices need to accept updates from a central operating location and admin users need to access the system. While operating on the premise of Zero Trust, the technology should still be accessible, usable and provide simple implementation. The implementation of the Zero Trust model in edge devices is crucial for securing connected places in the UK, and is a strategic response to the evolving threat landscape, ensuring the protection of national security and the privacy of individuals and government organisations.
National Security updates
Sign-up to get the latest updates and opportunities from our National Security programme.