Trends in the UK cyber insurance market
If you’ve held cyber insurance for a few years, you’ll have noticed big changes in policies, pricing, and the requirements for getting cover over that time. If you’re new to cyber insurance, you might be wondering whether it’s affordable for you, and what you’ll have to do to get cover. Let’s break down what’s going on with the cyber insurance market.
Background
Cyber insurance has its roots in policies written in the 1990’s, which were largely specialist addons to policies for technology companies. By the mid 2000’s insurers were offering policies in a similar form to modern cyber policies, with first-party cover offered for restoration of computer systems and business interruption costs, and third-party cover for claims brought against a company following a data breach or security breach.
Throughout the 2000’s and 2010’s, take-up of cyber insurance was low and growing slowly, claims were fairly rare, and claims costs were low. To increase uptake and gain market share, insurers offered low premiums and were able to place cover for smaller companies based on only a handful of basic questions. Because claims costs remained low, insurers could maintain low premiums without losing profitability.
The environment starts to shift
In 2017 the cyber landscape was changed by two major global cyber attacks, the most devastating of which being the NotPetya attack, which is estimated to have caused over $10 billion in damages globally.[1]
Despite these significant financial losses, insurance claims were limited due to the low uptake of cyber insurance at the time. These attacks would however signal to insurers the potential impact of unpatched software, and the scale of business interruption losses they could expect to see from a large-scale cyber attack.
At the same time, companies were gearing up for the 2018 implementation of the EU General Data Protection Regulation (GDPR). Most US states already had equivalent legislation in place, and GDPR brought data protection standards in across Europe, with fines for non-compliance of up to €20m or 4% of global turnover.[2]
In the following years, ransomware attacks increased and concerns over data protection and fines grew. By the end of 2019 insurers were paying out claims greater than the total of premiums they were collecting. Insurers therefore began increasing premiums and imposing stricter security requirements to reduce the number of claims.
The hard cyber market
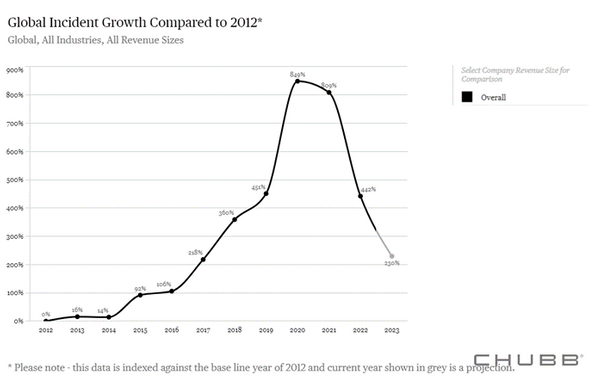
2020 saw a huge spike in cyber incidents, with data from Chubb showing that they handled almost double the number of incidents in 2020 compared to 2019.[3]
5
The majority of cost to insurers came from a significant increase in ransomware attacks. Ransomware is a type of software that encrypts a victim’s files, with the hacker demanding payment of a ransom in return for restoring the victim’s systems. Whether the ransom is paid or the systems are restored separately, there’s often a significant cost in loss of revenue for victims during the systems outage.
It’s unclear how much the COVID-19 pandemic impacted ransomware attacks, as ransomware incidents were already on a steep upward trajectory prior to the pandemic. The pandemic did however make people more aware of their reliance on technology, and the cost to their businesses of system outages.
As cyber entered a ‘hard market’, with prices increasing and cover harder to obtain, the general insurance market was also hardening. This meant that insurers could not mitigate cyber losses with profitability in other commercial lines of business.
Pricing
In response to the increase in claims, insurers adjusted pricing to reflect claims payments. Many larger companies saw their premiums double in 2021, and then double again in 2022. Small and micro-enterprises were less acutely hit, often seeing premium increases in the 30-50% range. In extreme cases, companies with usual risks and extremely high technology reliance saw premiums increase by 500% or more.
Security controls
The hard market brought with it a major focus on cyber security controls, with insurers scrutinising businesses through rigorous questioning. These long question sets delved into specific, technical controls, but largely revolved around basic areas of cyber hygiene:
- Access control – strong passwords, removing users when employment ends, and Multi-Factor Authentication (MFA).
MFA became the biggest request across the market, as it was felt that implementing an extra authentication step (such as a key code generator) would prevent the majority of ransomware attacks. MFA is often requested for remote systems access, and remote e-mail access, for example.
- Patching and updates – often a requirement to be applied within 7 or 14 days.
Ransomware attacks often involve exploiting software vulnerabilities, and software companies regularly release updates to patch these vulnerabilities. The longer it takes for patches to be applied the longer a company is vulnerable for.
- Backups – taken regularly, tested, and ring-fenced from the network or kept offline.
If a ransomware attack encrypts a computer system, the consequences will be fairly small where the company can simply restore their system from backup without paying a ransom.
- Ports – Closed or properly secured.
Ports are the connection between your system and external services. Some ports have to be open for basic services such as viewing webpages and receiving e-mails, others should only be open where specifically required, and some should never be open as they are outdated and insecure.
- Staff training – creating security awareness among employees.
Many cyber attacks involve an employee clicking on a bad link or providing their username and password to a fake person or website. Regular staff training can be indicative of a good management attitude towards cyber risk.
The cyber market today
Whilst cyber attacks remain frequent, they’ve dropped since 2020’s spike. Fears that the war in Ukraine would spill into global cyber attacks are so far unfounded[4] – perhaps as it’s keeping ransomware criminals operating in the area busy. Consequently, insurers are seeing a reduction in ransomware, and a commensurate increase in more traditional social engineering and funds transfer fraud crime.[5]
Small companies, who have seen smaller premium increases in the last few years, are seeing those increases drop to more manageable levels. Larger companies, having experienced significant increases in their cyber premiums, are often now seeing level rates or even rating reductions at renewal.
Cyber premiums won’t return to where they were in 2018, as those rates were unsustainable for any realistic claims scenarios, but premiums are now levelling out. For most companies, cyber insurance should be affordable, with cost dictated by their risks and level of cover required.
Similarly, insurers are now relaxing their requirements for security controls. Focus remains on access controls, patching, backups, open ports, and staff training, but requirements are now much less onerous. Many insurers also now use external vulnerability scans to aid their decisions, reducing the number of questions they need to ask clients in favour of an external survey of their network.
Ultimately, insurers are now able to make more proportionate decisions on cyber risk, with smaller, low-risk companies able to get cover without too many stringent requirements, and larger and higher risk companies needing to provide more in-depth information before obtaining cover.
[5] Cyber Insurance Academy, 2023
Cyber Resilience updates
Sign-up to get the latest updates and opportunities from our Cyber Resilience programme.













