Ensuring trust and protecting sensitive data in today’s digital world (Guest blog by Ultra)
It is widely known how detrimental data breaches can be for individuals and organisations. When that worst case scenario occurs, an organisation will experience one or more probable consequences: loss of sensitive, operational downtime, financial loss, reputational damage and potential legal action.
Unfortunately, we all live in time where the threat of these cyberattacks and data breaches are now constant. The ever-present threat landscape therefore prompts the question: How does an organisation secure data and ensure organisational integrity and trust in today’s digital age?
Building on that question, it is also nearly impossible to transact in this digital world without trust. The notion of digital trust is crucial in a global society where people often transact with people they have never met and may never encounter again. In fact, many transactions are not even between people at all, but between people and machines, or simply between machines. Examples are everywhere: automatic teller machines, electronic wire transfers and electronic filing of tax forms. Anywhere transactions are made, trust still needs to be established. In order to achieve that baseline of trust, assurance is needed in four main areas:
- All entities partaking in transactions are who they say they are.
- There is no breach of privacy/confidentiality.
- The intended transaction is the transaction that takes place.
- The transaction can later be proven to have taken place.
In today’s digital world, trust should be built on Public Key Infrastructures (PKI). So, what is PKI? PKI can be described as three things: a methodology, a technology and an infrastructure by which transactions can be performed. The method relies on the presentation of trusted digital certificates between all parties in a transaction. The simple rule of engagement is: if you have a certificate that I trust, then I can also trust you, and vice versa. Typically, end entities are configured with one or more trust anchors which are then used as a starting point to validate a given certification path. The technology used is cryptography. More specially, Public Key Cryptography. This also where Hardware Security Modules (HSM) plays a role as the root of trust which protect PKIs from breaches. HSMs enable the generation of keys throughout the PKI lifespan, while ensuring scalability of the whole security architecture.
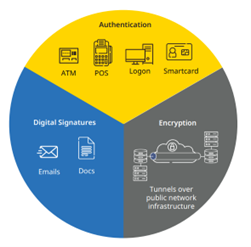
PKIs govern the issuance of digital certificates to protect sensitive data, provide unique digital identities and secure end-to-end communications. By using digital certificates, PKIs encrypt and decrypt to verify both user and machine identities in order to prove the integrity of digital transactions. The HSM is used to secure all cryptographic processes through generation, management and protection of keys used for encrypting and decrypting data.
Using public key encryption mechanisms, the HSM generates two keys that have a mathematical relationship such that a message enciphered with one of the keys can only be deciphered by the other and vice versa. One of these keys is kept private and the other made public. So why are HSMs important to the PKI and HSM security infrastructure?
HSMs provide the physical separation for cryptographic operations and key material. Their software and hardware is specifically dedicated to providing cryptographic operations; it can be specifically optimised for that purpose. Also, HSMs perform cryptographic operations faster and with higher assurance than their software counterparts. For example, one of the key steps in generating public/private key pairs for certificate, entails the generation of random numbers. HSMs has the dedicated hardware specifically designed to generate those random numbers. Therefore, they can generate numbers that have greater entropy than would be the case if the hardware were not specifically designed for that purpose. Lastly, HSMs are standard compliant computing devices. An example of a technical standard is Federal Information Processing Standard (FIPS) 140-2, a U.S. government standard covering the implementation and assurance of security mechanisms such as algorithms and tamper protection.
Ultra believes in this approach to cyber-security posture reinforcement. HSM solutions such as Ultra’s KeyperPlus offer the most modern security features for the management and storage of cryptographic keys, and to the highest level of security achievable.
Help to shape and govern the work of techUK’s Cyber Security Programme
Did you know that nominations are now open* for techUK’s Cyber Management Committee? We’re looking for senior representatives from cyber security companies across the UK to help lead the work of our Cyber Security Programme over the next two years. Find out more and how to nominate yourself/a colleagues here.
*Deadline to submit nomination forms is 17:00 on Tuesday 18 October.
Upcoming events
Get involved
All techUK's work is led by our members - keep in touch or get involved by joining one of the groups below.





